Did you know that it’s very easy to tap a mobile phone nowadays? It’s a scary thing to think about, but it’s true. As technology improves, so do the many ways that phone tapping can happen. Now, malicious individuals can install spy apps like mSpy on your phone and you’d never even think it was there unless you know what to look for. Because I don’t want anyone’s privacy to be violated, in this article, I’ll discuss what to do if your phone is tapped and how you can prevent it from happening again.
How Do You Know If Your Phone Is Tapped?
Before I go on, it’s important to determine whether or not your phone is being tapped in the first place. Spy apps usually come with stealth options, so if you don’t suspect anything happening in your device, you likely won’t be able to tell anything. However, sometimes, there are physical signs that your phone is being tapped. Luckily, if you know what to look out for, these signs should be easy enough to spot.
Battery Consumption
One of the most telling signs that your mobile phone is being tapped or monitored is if there’s suddenly unusual battery consumption. If there’s a spy app such as mSpy installed on a device, it means that it has to operate in the background 24/7 for all the features to work. Naturally, this consumes more battery. It will also result in the phone being hotter than usual since it has to work hard to do all its tasks. This is significantly more telling if it starts out of nowhere. For instance, if you’re a gamer and you play games often, you shouldn’t be surprised if your phone feels hot to touch and drains faster than normal. After all, gaming is very heavy on your phone’s processor. But if you’re not doing something particularly processor-intensive, you should probably be suspicious. In other words, if your phone suddenly becomes hot and drains fast, even while you’re not doing anything heavy, like games or online streaming, then this is a good sign that your phone might be tapped.
Data Usage
Spy apps need the internet in order to operate. After all, they use your phone’s data to send information from the target device to the app’s online platform so that a third party can view it. Therefore, if you’re experiencing a sudden rise in data consumption, your mobile device could be tapped. This could be more noticeable if your phone’s on a limited data plan. If your mobile data used to last you weeks but now only lasts you a few days, you should begin to worry. However, if you have an unlimited data plan, you may not be able to notice the problem. To confirm whether your mobile data consumption has been rising abnormally, it’s best to download an external app, like My Data Manager on Android or Data Manager on iPhone, that will chart your daily, weekly, or monthly data usage.
Uncommon App/Hardware Behavior
Unsurprisingly, spy apps can affect how your phone performs. Aside from data and battery consumption, your phone can also exhibit unprompted behavior related to your apps and hardware. Some the behavior to watch out for are:
If it automatically lights up, even when you’re not using itYour device randomly taking screenshotsSound recording or video recording apps randomly starting upStrange pop-up ads where there shouldn’t be anyYou see unknown apps installed on your deviceYour phone doesn’t allow you to uninstall specific apps or any apps at allDevice performance is dropping, with lags, ghosting etc.
Take note that if you have an old or malfunctioning device, some of these symptoms might just be a sign that you need to buy a new phone. However, if you see several of these symptoms together, especially the more suspicious ones, like strange pop-up ads and unknown apps being installed, then it’s very telling of a phone tap. You should be more concerned if you also see unusual battery consumption and data usage, as discussed above.
What To Do If Your Phone Is Tapped
Now that you recognize the signs your phone is tapped, what should you do? In this section, we’re going to discuss your best action plan for when you realize that your privacy is being violated.
Check Your Phone For Any Malicious Elements
If you’ve checked most of the boxes in the previous section, then you should already have strong suspicions that your phone is being tapped. Nevertheless, you still need to know how exactly your mobile phone is being monitored. You can do this by implementing various checks on your phone.
Check For Spyware
Installing spyware, such as mSpy and WebWatcher, is one of the most popular ways to monitor a mobile device nowadays. If you suspect that your phone is being tapped, the first thing you should look for is whether it has spyware installed. You can easily check for spyware by installing an anti-spyware tool from the Google Playstore. Apps such as CyberTor can scan your mobile device and determine if spy apps are on your phone. If it finds any, the app will allow you to uninstall them in just one click. Most of these apps have paid advanced features, but even the free basic version should be enough if you only want the monitoring service gone. Pro Tip: If you want to compile evidence for possible police action, you should take screenshots of the scan results from the malware scan.
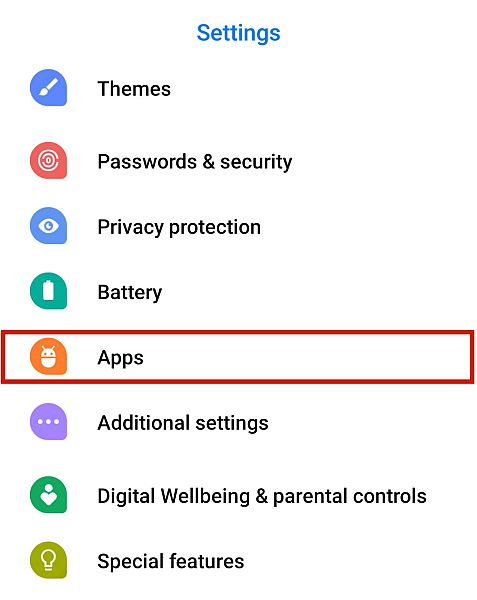
Check For Unsafe Applications
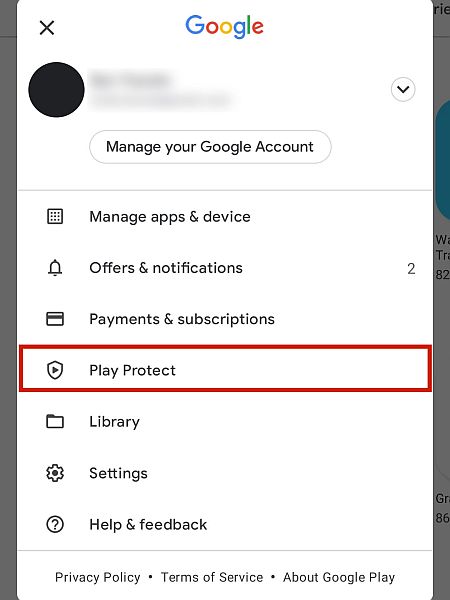
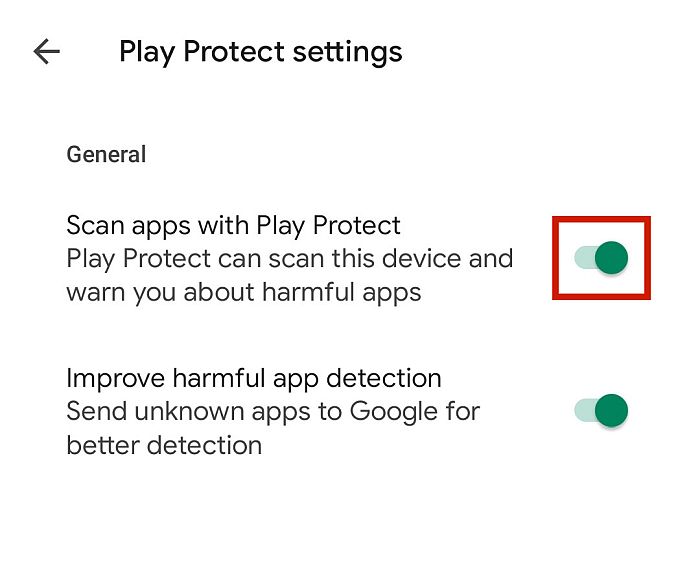
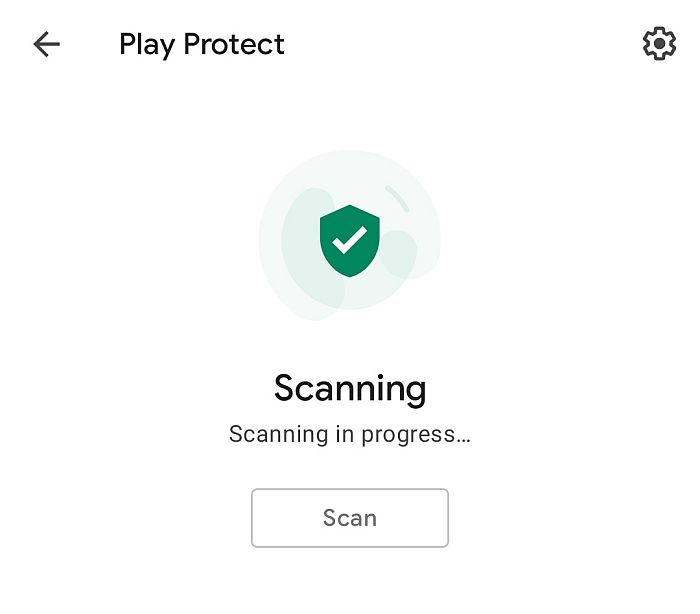
Although installing a spy app is one of the easiest ways to monitor a mobile device, it’s not the only way. Malicious apps, typically those that contain a virus, can also tap your phone without your consent. You can use the Google Play Protect feature to scan your Android device for any vulnerabilities with just a few steps.
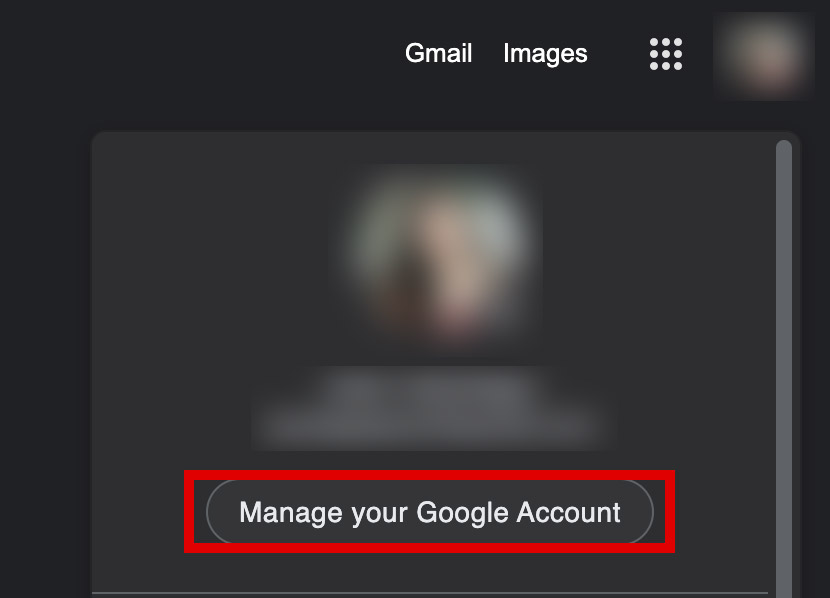
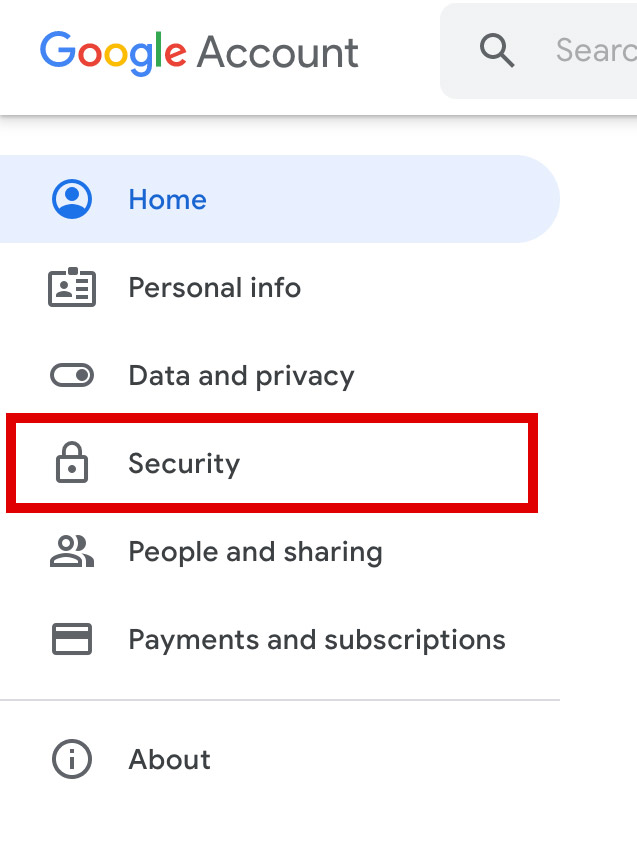
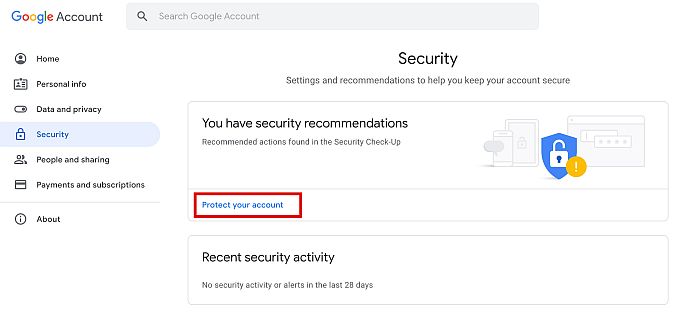
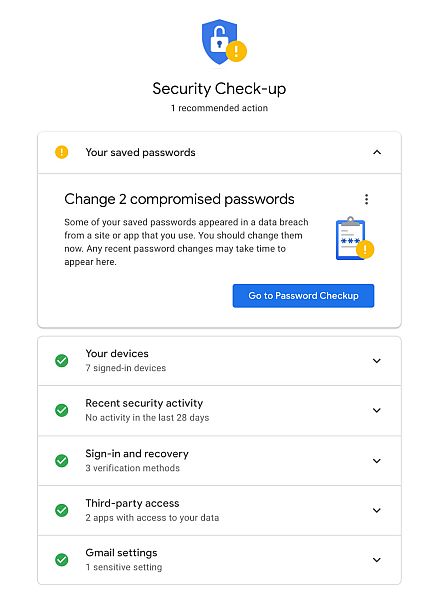
Initiate A Google Accounts Security Checkup
This security breach could compromise your Google Account. To make sure no hacker or stalker has access to your Google Account, you should protect your account by doing a security checkup.
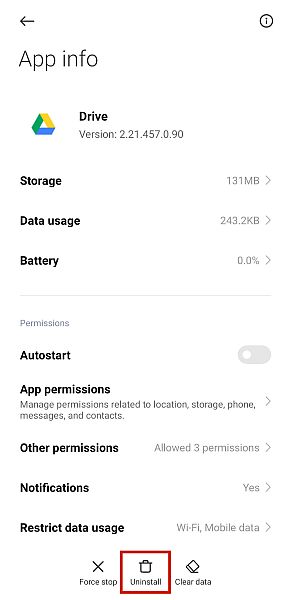
Remove Apps You Don’t Trust
When checking for security breaches on your phone, you will want to remove any unnecessary, untrusted, and unknown apps from your phone. You can do this by following these steps.
Do Some Damage Control
If you did your security checks properly, you may have found some malicious apps or spyware on your mobile phone. Now that you know your privacy has been violated, it’s time to control the damage that these apps can do. You can’t do anything about the information already leaked, but you can prevent more of your sensitive data from going out. For the damage control steps, follow the directions below.
Get A Burner Or Prepaid Phone
If you discover that your phone is being monitored, you can get yourself a cheap burner or prepaid phone as an alternative means of communication, at least until you solve the problem. You can use this device in the meantime for contacting family and friends, authorities, and other important contacts. Keep in mind that some spy apps have a sim removal alert feature, which will notify the user of the spyware when your device is disconnected from its sim. If you don’t want to risk this, you should get a different sim card, as well. This way, you avoid further data leaks, and whoever is on the other end of that spy app won’t realize that you know what they’re doing.
Notify Important Contacts
One of the many problematic things that a phone tap can do is to involve all your contacts. If your cell phone is hacked, your contacts’ personal information, such as contact numbers and addresses, is also revealed. Because of this, you will have to tell all of your important contacts to stop communicating with your tapped phone number as soon as possible, especially those from work or business. Use your untapped, temporary phone to contact everyone you need to and inform them that your device has been compromised.
Compile Evidence
An invasion of privacy is a serious offense that’s punishable by law. Due to this, you can bring this case to the proper authorities, who usually have special equipment that may help you catch the culprit. However, all this is only possible if you have sufficient evidence. Granted, gathering evidence of phone tapping isn’t as easy as it sounds. If you notice a pattern, you can try to predict it and capture instances of your phone lighting up, using the speaker, or using the camera on its own. You can also take screenshots of the scan results from whatever anti-spyware app you might download. Other than that though, you don’t have many other options. If you do manage to get enough evidence, you can even bring the case to a lawyer, who should advise you on other steps that you can take – especially if you have a suspect in mind.
Report Any Evidence Of Violations To The Proper Authorities
Once you’ve gathered enough evidence, you can now submit the case to the appropriate authorities. As mentioned, your local police department should help you with issues like this, but only if you have sufficient evidence. For special cases of phone tapping because of domestic violence, you may dial 1-800-799-SAFE from another device. This number belongs to the National Domestic Violence Hotline. You can also text “Start” to 88788.
Prevent Your Phone From Being Tapped Again
Hopefully, you now know how to detect a tapped device, and you’ve already taken the appropriate steps to report and delete it. Even if you’re not being spied on by anyone anymore, the battle still isn’t over. You now know firsthand the dangers of illegal phone tapping, and you should do your best not to go through the same things again. To prevent that incident from ever happening to you again, follow these security steps.
Install Anti-Spyware Software
Installing an anti-spyware app will make it more difficult for potential malicious people to do anything against you. This is the best passive method you can use to guard against spyware. With anti-spyware software, you will be notified whenever you have malicious apps installed on your phone – even if you didn’t notice it. Most apps like this have a paid version for their more advanced features, but for basic security scans, the basic free subscription should be enough. You can upgrade when you feel like your cell phone is in danger again, or if you just want more features.
Only Use Secure Passwords
Passwords are some of the most overlooked security features that we all encounter every day. Many people seem to forget this, but it’s important to always use unique, secure passwords. Make sure that you comply with the website’s standards for what a strong password is. Usually, this includes alpha-numeric characters, symbols, uppercase letters, and more. This will make sure that your password is harder to guess. For instance, the password [email protected] is much more secure than 1waffles2. Additionally, make sure to never use just one password for all of your accounts. If you only have one password for everything and you unknowingly register into a site with poor site security, hackers will easily have access to all of your accounts, even if they just managed to hack that one weak site.
Use A Password Manager
Let’s say that you’re willing to use a unique, strong password for each of your online accounts. That’s great! But how are you going to remember them all? If your answer is to write them on a piece of paper somewhere, you’re wrong – and in danger. Luckily, that’s what password managers are for. Password managers are secure online vaults that only you have access to. Think of a safe with one master password. Inside the safe, all of your passwords and sensitive notes are stored. Apps like BitWarden and LastPass Password Manager usually come in the form of browser extensions that you can easily toggle on or off. There are even some that automatically fill the fields of recognized websites. If you have a secured password manager, using unique and secure passwords for all of your accounts becomes a piece of cake because you don’t have to remember each one of them. However, you have to make sure that you do your research when choosing your password manager.
Never Let Someone You Don’t Trust Use Your Phone
You would be surprised to know how quickly you can install a spy app on a mobile device. In fact, it can take as little as 5 minutes for some apps. This means that you should avoid handing over your cell phone to anyone that you don’t personally know and trust, especially if it’s a stranger. If someone you don’t trust asks to use your device, politely refuse. You don’t even need to tell them that you have sensitive information on your phone. Instead, tell them you’ll send a message or call someone on their behalf. Another solution is to have a ‘public’ device that you use moderately and lend to other people. It shouldn’t contain any private information, which will be on your main, ‘private’ device. However, for many, the latter method is quite excessive. Refusing to lend your phone is simply the most practical option.
Only Install From Trusted Sources
Your device has a setting that warns you if you’re installing an app from an untrusted source – usually, this happens when you’re installing from outside the Google Playstore. To minimize the risk of installing malicious apps or viruses, only install from verified sources like the Google Playstore. After all, almost everything you need is going to be there anyway. If you ever need to install something that isn’t on the Playstore, make sure that it’s not a virus. Install only from a reputable site, and read comments and reviews about the APK first before you download it. Here’s a helpful tutorial to know if an APK is safe.
Don’t Leave Your Phone Switched On When You’re Not Using It
If you’re still worried about potential spies, another thing you can do is to turn off your phone when you’re not using it. Spy apps can only operate if your phone is turned on, so if there is one installed on your device, it won’t be able to gather information about your location or surroundings with your phone turned off. More than that, some malicious apps may not let you turn your phone off, so you’ll know the moment you turn it off whether malware has been installed on your phone or not.
Disable Bluetooth When Not In Use
Similarly, you should also turn off your Bluetooth when you don’t have any of your devices connected to it – especially if you’re in public. Files can be sent and installed on your phone via Bluetooth, so leaving it open for connection increases the chances of a malicious actor connecting with your phone and sending malicious software over. All in all, it’s always safer to just turn your Bluetooth off when it’s not in use.
Make Sure Your Phone Isn’t Tapped!
Now that you know how to check for signs of phone tapping, you also know what to do if your phone is tapped. Some of the things that can do include:
Check for spyware and unsafe applicationsInitiate a Google Accounts Security CheckupUninstall apps that you don’t trustPrevent your phone from being tapped again
Remember, phone tapping is a serious violation of privacy, so it’s right for you to be alarmed. If you have suspicions that your phone is being monitored illegally, don’t just dismiss it as nothing and act now. Did you like this article? Let me know in the comments below!